
Definition: Cyber Hygiene Cyber Hygiene Steps You Need To Follow To Improve Online Security Conclusion: Make Cyber Hygiene Pattern Part Of Your Routine
Much like any individual who follows basic personal hygiene rule to maintain overall well-being, Cyber Hygiene are basic steps that everyone should follow to keep their data intact& machines well-protected.
Definition: Cyber Hygiene
In layman expressions, Cyber Hygiene can be defined as the steps or a number that every computer& portable customer should adopt to maintain system health and data security. These stairs majorly include danger mitigation tricks& cybersecurity recommendations to prevent illness& virus attacks.
With brand-new teleworking criteria, cyberattacks have become more frequent and sophisticated. Hence, with flexibility there comes huge responsibility to improve online security and maintain devices in good shape. Fortunately, we have a basic Cyber Hygiene Checklist gave assurances that we control our computers, portables and other manoeuvres with relevant care.
Cyber Hygiene Steps You Need To Follow To Improve Online Security
Without using the right tools, maintaining personal cleanlines can be a complex process. Similarly, without consuming the claim products and services, organizing good cyber cleanlines, isn’t possible.
Note: Make sure you install and use reputable curricula& application. Keep your research thorough and download everything from trustworthy sources.
Stair 1- Run The Right Antivirus Program
Installing a trustworthy antivirus or anti-malware program across all your devices, can certainly help you get 360 -degree protection in the events of phishing affects or an attempt to exploit a vulnerability. Make sure you prepared the security solutions to perform automatic and regular scans.
We have prepared a complete list of Best System& Mobile Security Solutions, so that you have to research little, when it comes to choosing the right antivirus software.
Best Paid& Free Antivirus For Windows
The Best Antivirus Software For Mac
Best Free Antivirus Apps For Android
Best Free Antivirus For iPhone

Download Systweak Antivirus
STEP 2- Use Network Firewalls
Activating a Network Firewall is probably another excellent tactic to maintain good cyber cleanlines. These Firewalls act as the first path of defense in network security by frustrating unauthorized consumers from accessing your forward servers, websites& other sources that can be accessed from the web.
Considering the significance of network firewalls- corporate companies, institutions, and establishments should feed them to secure their networks.
10 Best Firewall Software For Windows 10, 8, 7 PC
STEP 3- Keep All Your Software& Programs Up-To-Date
Hackers& cybercriminals are always looking for new and multiple ways to perform security transgress. Feeing old-fashioned or infected curricula opens the doors for intruders to manipulate vulnerabilities. So, the best bet to keep those doorways closed is by ever modernizing your software. This certainly reduces the probability of your maneuver getting attacked.
Since it can be a difficult& time-consuming process to keep all the lay programs on your system up-to-date regularly. You can take the help of a dedicated software updater that clears the entire process hassle-free. Systweak Software Updater is a one-stop solution that comes with a crowd-sourced repository of popular and commonly used software that fulfills daily needs& requirements. It speedily downloads& invests the newest and most compatible versions of different kinds of utilities in no time.
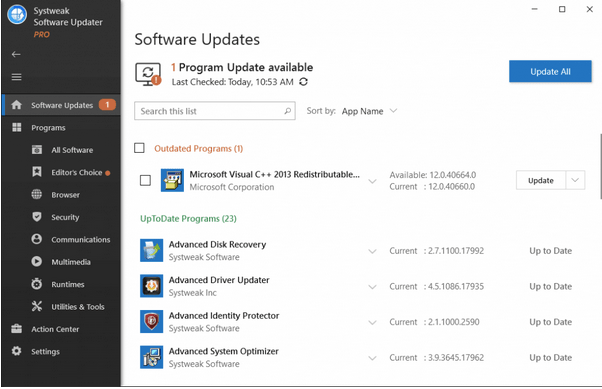
Download Systweak Software Updater
STEP 4- Set Complex& Unique Passwords
According to several insurance studies, the most commonly used web passwords are’ 12345678 ’ and’ password’. Undoubtedly, they are easy to remember, but they are certainly easy to spoof. And, if you are using the same password across multiple websites& details( which almost 92% of users do) it employs your data at increased risk. An standard password should be combined of at least 12 personas( consisting of numbers, epitomizes, symbols( with uppercase& lowercase )) or you can follow the step-by-step guide to create strong passwords& recalls that it.
Alternatively, you can use the Best Password Manager like TweakPass that gives you the ability to remember simply one Master Password instead of obstruct an history of several passwords for many details. You can even experience aspects like Password Generator to create unique, complex& strong passwords, which guarantee solid terms of protecting your reports and secure your data.
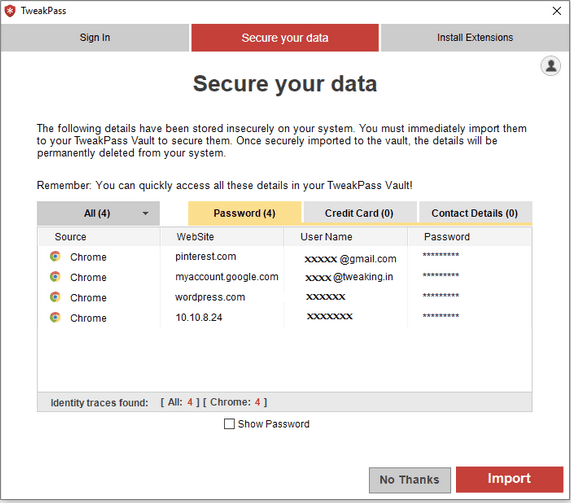
Download TweakPass
STEP 5- Employ Device Encryption
Although most fellowships& firms have their data encryption handles in place. But as we move to remote working, encrypting personal maneuvers have become a quintessential need. Although, a majority of the members of laptops& smartphones, encryption is standard; while certain works use end-to-end encryption functionality to safeguard data or conversations.
Alternatively, you can use an encrypted USB memory stick for protecting your sensitive enters or back up important data to the cloud service.

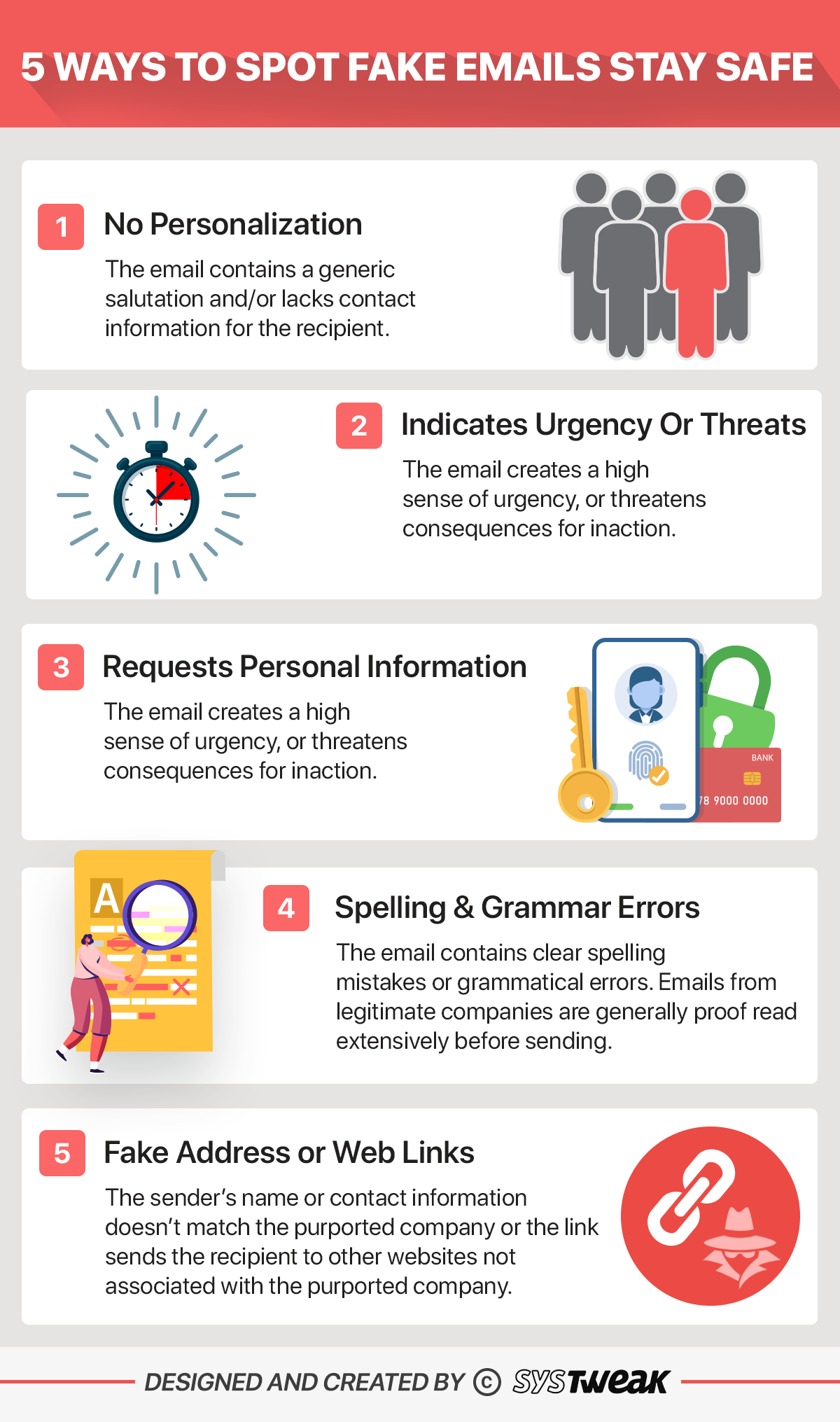
STEP 6- Beware Of Suspicious Apps& Websites
Due to the coronavirus outbreak, intruders are finding new ways to steal users’ data. They are developing harmful websites and apps that access users’ personal information. They even use emails or verse senses to trick you into installing malevolent employments, which further steal your credentials, chronicle numbers, Social Security figures& more.
These scammers implement brand-new tactics to affect customers through emails/ defraud themes, but there are some clues you can consider to spot fake or scam emails easily.
STEP 7- Keep Your Hard Drive Clean
Clean your machine and data the proper way. Before selling your smartphone, laptop, or tablet, make sure your personal, financial, or sensitive intelligence doesn’t get progressed along. When you keep your device scavenged, it certainly closes the potential loopholes that can give scammers the opportunity to access or control your structure or mobile.
Using a reliable PC Cleaning Utility like Advanced System Optimizer is the best bet to keep your entire structure clean and if wishes to permanently get rid of records containing feelings message, it does have a potent Shredder feature that reaches your undertaking hassle-free. You can also take a look at the following useful guides to permanently clean sensitive data on different inventions 😛 TAGEND
Download Advanced System Optimizer
Best Data Shredder Software for Windows 10, 8& 7
Best File Shredder Software For Mac
Best File/ Data Shredder Apps To Permanently Delete Data From Android

STEP 8- Use Reliable VPNs
Nothing can beat a VPN service if you want to enjoy top-notch online privacy and obscurity. Creating a private system substantiates a protected and encrypted bond, which stops hackers from envisioning or accessing your confidential intelligence. You can easily mask your IP address and bypass geo-blocks and censorship without any hassles.
If you want to enjoy complete freedom while browsing the web& not worry about sounding malevolent websites, ads, or trackers, use Systweak VPN. It helps users to address all of their Internet traffic to one of their servers, where everything is encrypted. To know more about Systweak VPN, click here!

Here are some helpful associates related to using VPN service on different manoeuvres 😛 TAGEND
Best VPN For Windows 10, 8, 7 PC
Best Free VPN For iPad and iPhone
STEP 9- Safeguard Your Sensitive Data
“There were 1,473 reported data infractions in 2019, according to the Identity Theft Resource Centre’s End-of-Year 2019 Data Breach Report. That represents a 17 percent multiply over 2018. ”- Norton
If you’ve ever become a victim of identity scam, knowing how to report is a fundamental step. On the other side, practising good cyber cleanlines, by impede all your feelings, personal, and business data in a lock crypt is a quintessential process more. Apart from following all the aforementioned Cyber hygiene gradations, it is essential that you scan your system regularly to see any privacy exposing cloth& if known stored under a self-assured arch or shred permanently. While executing the entire process can be a tricky business, you can certainly take help from Best ID Theft Protection Service like Advanced Identity Protector, to accomplish the part enterprise like a breeze. Visit Website

Identity Theft Statistics That May Surprise You
Top 9 Best Identity Theft Protection Service
13 Ways To Protect Yourself From Identity Theft
Five Smart& Promising Ways To Deter Identity Fraud
Conclusion: Make Cyber Hygiene Practice Part Of Your Routine
Well, Cyber Hygiene is all about civilize yourself to behave in a proactive way when it comes to maintaining cybersecurity, just like the nature you take care of your physical hygiene. Regrettably, Cybersecurity is still something make’ for granted’, nonetheless, this will soon change, as cyber menaces continue to grow& become more robust and boosted than ever. Meanwhile, we recommend our books to establish solid Cyber Hygiene Practices with the steps mentioned above.
Still have any queries? Want to get in touch with a Cybersecurity Expert? Write to us at support @systweak. com
NEXT READ: 9 Ways To Erase Your Digital Footprint From The Internet !
The post Up Your Cyber Hygiene Game: Best Practices To Improve Online Security sounded first on Systweak Software.
Read more: blogs.systweak.com







Recent Comments